Extracting bastion credentials
Extraction from AWS console
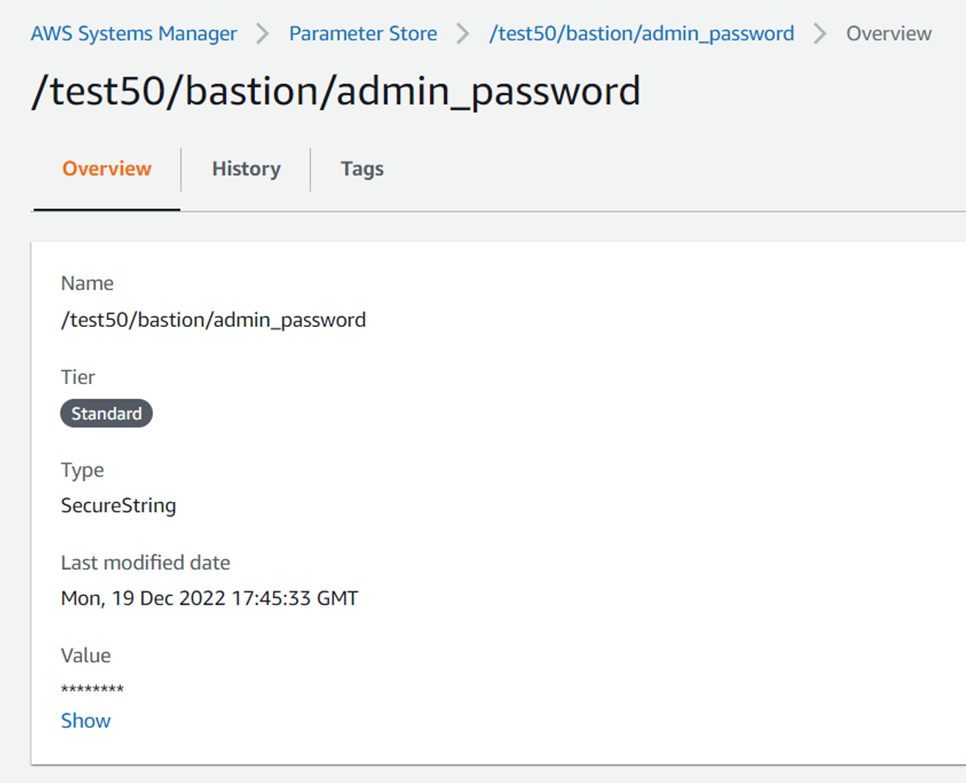
To extract the bastion password, you can log into the AWS console and go to AWS System manager > Parameter Store > <top_level_fqdn_prefix>/bastion/admin_password and Click “Show”. Please see example below.
Extraction from CLI
To perform these actions, the following pre-requisites need to be fullfilled:
An AWS profile
AWS cli installation
The following information is required for running the command
the AWS region where the cluster is deployed (chosen at deployment time)
The AWS profile that has the relevant credentials to access the SSM store
The relevant details for the above can be found in the following section
https://docs.siemonster.com/current/command-line-tools
The bastion password is stored in AWS SSM and is generated at the time of the cluster deployment. Below is an example cluster URL and then the steps to perform the password extraction
Example URL:
https://tenant1.example.siemonster.io
Command Example:
aws --region us-east-2 ssm get-parameter --name /example/bastion/admin_password --with-decryption
Example output:
{
"Parameter": {
"Name": "/example/bastion/admin_password",
"Type": "SecureString",
"Value": "XXXXXXXXXXXXXXXX",
"Version": 1,
"LastModifiedDate": "2022-12-19T17:45:33.355000+00:00",
"ARN": "arn:aws:ssm:us-east-2:000000000000:parameter/example/bastion/admin_password",
"DataType": "text"
}
}The “Value” line is the item that needs to be used as password for the bastion HTTPS and OpenVPN access.
The Username for the bastion HTTPS and OpenVPN access will always be admin
NOTE: All credentials (username and password) are case sensitive unless the contrary is stated.
