KB - Migrating Suricata IDS to persistent configuration
On the SIEMonster Hydra log aggregator there is a service named Suricata that performs intrusion detection on the network layer. In some cases it may be preferred to deviate from an out of the box configuration to a persistent configuration that allows for disabling rules and/or modifying other configuration items for the solution. To do so the configuration files need to be mapped to persistent storage. This can be done by performing the following steps in sequence.
#Preparing folder structure for persistent data
mkdir -p /data/suricata/config
mkdir -p /data/suricata/update
#Copying the relevant files
docker cp suricata:/etc/suricata/. /data/suricata/config/After the copy is done, please check to see if your file system looks like this
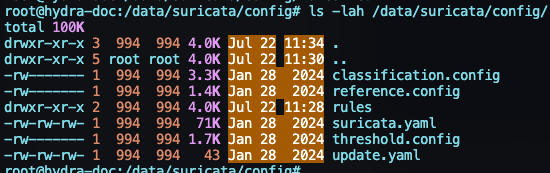
The next step is to modify the Systemd Unit files so that the correct paths are mapped as volumes. The follow two line items need to be added
-v "/data/suricata/config/:/etc/suricata" \
-v "/data/suricata/update/cache:/var/lib/suricata/update/cache" \To make the change perform the following steps:
Type vim /etc/systemd/system/suricata.service and Press [ENTER]
Next Type :set mouse= and Press [ENTER]
🔖 The above is to disabled visual mode in vimNext Press i or [INSERT]
Move to the end of the line that matches the sample below and Press [ENTER]
“-v "/data/suricata/config/:/etc/suricata" \ -v "/data/suricata/update/cache:/var/lib/suricata/update/cache" \”Copy the two lines from the above code sample and Paste it into the file. It should look like below when you have done it correctly.
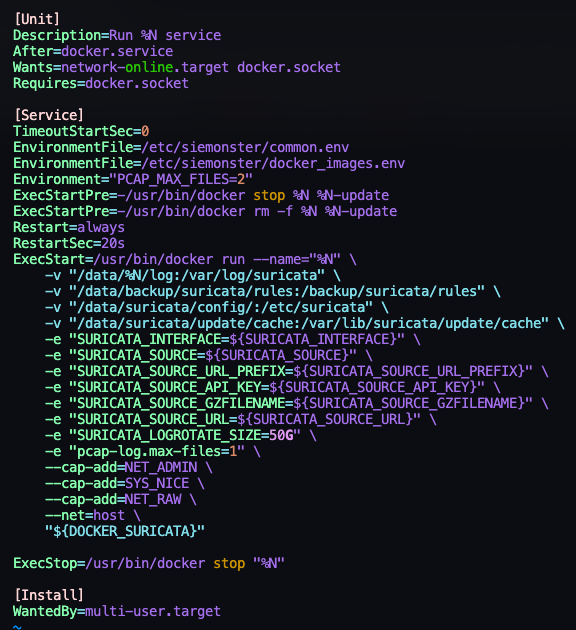
Press [ESC] and then Type :wq and Press [ENTER]
Now Run the following commands in sequence
 Please wait for a few seconds between commands to ensure the previous command has completed.BASH
Please wait for a few seconds between commands to ensure the previous command has completed.BASHsystemctl daemon-reload systemctl restart suricata docker exec -it suricata suricata-update update-sources docker exec -it suricata suricata-update
Your Suricata instance should now have a persistent configuration so you can make changes to it that will persist through reboots.
![]() IMPORTANT: The suricata.yaml configuration file is yaml, it is extremely sensitive to tabs. Adding a tab anywhere in the configuration file will break the configuration and prevent the system from starting. It is extremely important to make backups of the file before you make changes so that any changes made can be rolled back.
IMPORTANT: The suricata.yaml configuration file is yaml, it is extremely sensitive to tabs. Adding a tab anywhere in the configuration file will break the configuration and prevent the system from starting. It is extremely important to make backups of the file before you make changes so that any changes made can be rolled back.
