Threat intelligence attributes
LIst attributes:
Attributes in MISP can be network indicators (e.g. IP address), system indicators (e.g. a string in memory), or even bank account details. MISP attributes are purely based on usage (what people and organizations use daily).
A type (e.g. MD5, url) is how an attribute is described
An attribute is always in a category (e.g. Payload delivery) which puts it in a context
A category is what describes an attribute
An IDS flag on an attribute allows to determine if an attribute can be automatically used for detection
To access the list of attributes, click List Attributes on the left pane, The Attributes page opens, that displays a list of last 60 attributes.
🔖 NOTE: If you have a large number of feeds enabled, it is not recommended to view attributes like this as there are millions captured between all feeds, it’s better to search through the events for specific attributes.
The Events page displays the following information:
Event: This is the ID number of the event that the attribute is tied to. If an event belongs to your organization, then this field will be colored red.
Org: The organization that has created the event
Category: The category of the attribute, showing what the attribute describes (for example the malware's payload)
Type: The type of the value contained in the attribute (for example a source IP address)
Value: The actual value of the attribute, describing an aspect, defined by the category and type fields of the malware (for example 1.1.1.1)
Comment: An optional comment attached to the attribute
IDS: Shows whether the attribute has been flagged for NIDS signature generation or not
Distribution: Describes who will have access to the event
Actions: A set of buttons that allow you to edit or delete the attribute
Search attributes:
Data contained in the value field of an attribute can be searched. You can search for attributes based on contained expression within the value, event ID, submitting organization, category and type. To search for attributes, click Search Attributes on the left pane, The Search Attributes page opens.
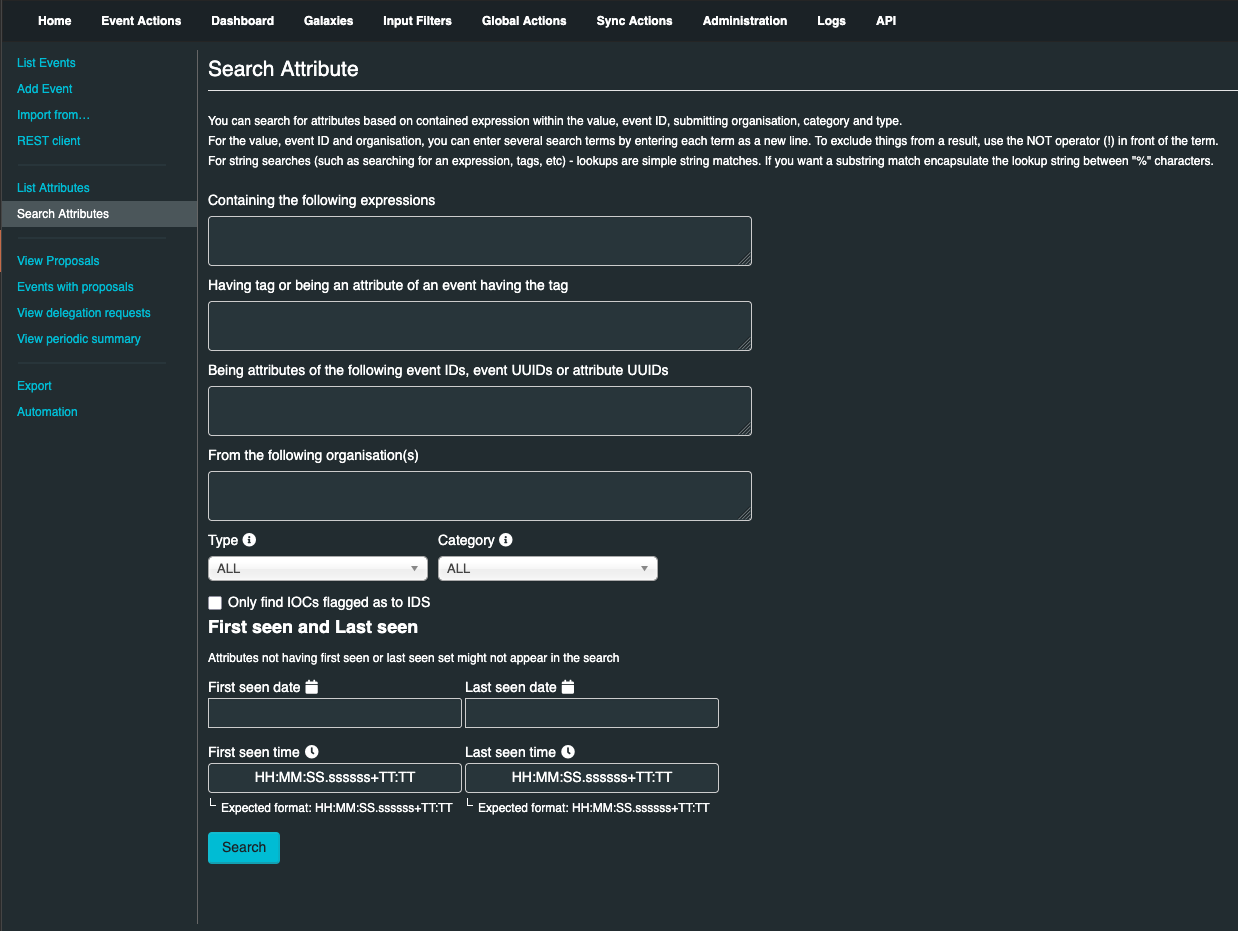
For the value, event ID and organization, you can enter several search terms by entering each term as a new line.
To exclude things from a result, use the NOT operator (!) in front of the term.
For string searches (such as searching for an expression or tags) - lookups are simple string matches.
If you want a sub-string match encapsulate the lookup string between "%" characters.
Apart from being able to list all events, it is also possible to search for data contained in the value field of an attribute, by clicking on the "Search Attributes" button.
